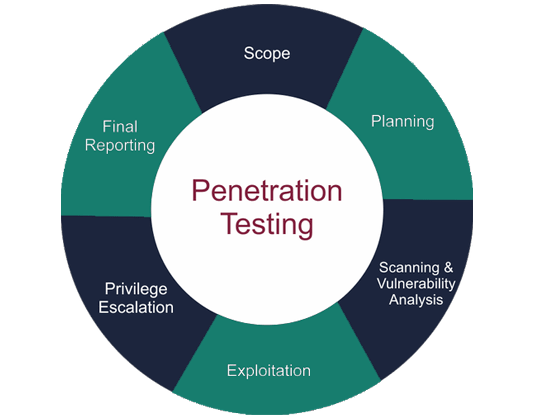
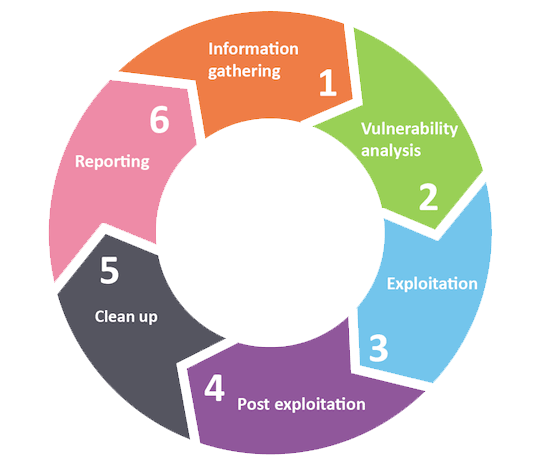
ORM (Online Reputation Management)
Reform your online presence through dedicated Reputation Management Services.
Company / Brand Reputation Management
Adopt brand reputation services for a memorable and sustainable experience.
Online Surveys
Market Research Survey, Brand awareness survey, Customer Satisfaction Survey, Lead generation survey
Articles & Blog Posts
Campaign-oriented article will incorporate your marketing goals and target audience.